AI Summary
If you accept payments through WordPress forms, there’s an important connection between payment security and email deliverability that you should know about.
Card testing fraud is a common practice carried out by cybercriminals, who use automated bots to validate stolen credit cards on your payment forms. These card testing attacks are not only bad for security, but they can also impact your email sender reputation in ways that affect your legitimate business communications.
Here’s why: Each payment form submission typically triggers an email notification. During a card testing attack, hundreds or thousands of fraudulent attempts can generate a sudden spike in your outbound email volume. This pattern can signal to email providers that something unusual is happening with your domain, potentially affecting how your emails are delivered.
But there’s no need to panic! With the right preventive measures in place, you can protect both your payment forms and your email infrastructure.
Let’s explore how card testing fraud works and the practical steps you can take to safeguard your WordPress site.
- What Is Card Testing Fraud?
- Volume Spikes vs. Spam Complaints: Understanding the Difference
- Timeline: How Card Testing Attacks Affect Email Delivery
- How to Prevent Card Testing Fraud
- The Complete Email Protection Strategy
- Recognizing Card Testing Activity Early
- Email Deliverability Recovery Steps
- Next, Find Out More About How To Improve WordPress Email Security
What Is Card Testing Fraud?
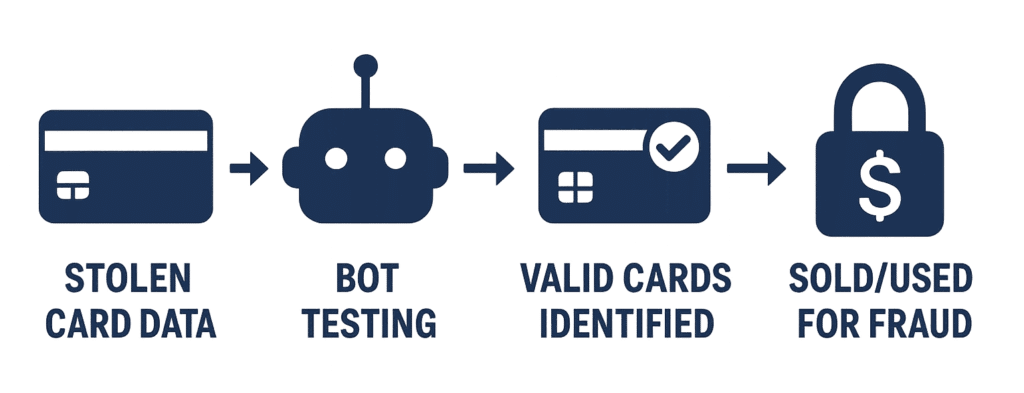
Card testing fraud (also called “carding” or “card checking”) is when criminals validate stolen credit card numbers by making small test purchases on your website.
Fraudsters purchase lists of stolen credit card data from the dark web, sometimes thousands of card numbers at once. But they don’t know which cards are still active, which have been canceled, and which will trigger fraud alerts. So they test them.
They use automated bots to rapidly submit small transactions, typically between $0.50 and $5.00, through payment forms that accept variable payments (donation forms are a common target.)
These amounts are small enough to avoid fraud detection systems, below the threshold that would alert cardholders, and fast to process, allowing hundreds of tests per hour.
Once a card successfully processes a transaction, the fraudster knows it’s valid. These verified card numbers are then sold at a premium on the dark web or used for large purchases before the cardholder notices.
Why are WordPress sites prime targets?
- Market share: WordPress powers 62% of all websites with a content management system, making it the most common platform on the web
- Varying security levels: Smaller businesses often lack the sophisticated fraud detection systems used by large enterprise e-commerce platforms
- Easy accessibility: Payment forms are publicly accessible and easy to locate through automated scanning
Email Deliverability & Card Testing Fraud
Here’s where things get even more tricky for site owners: A single card testing attack can generate 500 to 5,000 transaction attempts per hour, and each one triggers an email notification from your site.
When fraudsters test 1,000 stolen credit cards on your payment form in 2 hours, your WordPress site sends 1,000 notification emails from your domain in those same 2 hours.
How Email Providers Evaluate Sending Patterns
Email providers like Gmail, Outlook, and Yahoo use automated systems to evaluate sender behavior. These systems analyze patterns including sudden changes in email volume from a domain, consistency of sending patterns over time, engagement rates and bounce rates, and authentication protocols.
When a site’s email volume suddenly increases by 10-20x (which can happen during card testing attacks), these systems may flag the pattern as unusual. The challenge is that automated systems can’t easily distinguish between legitimate volume increases and potentially problematic activity.
Understanding Sender Reputation
Internet Service Providers (ISPs) use volume consistency as one of several trust signals when evaluating email senders. They generally prefer predictable sending patterns.
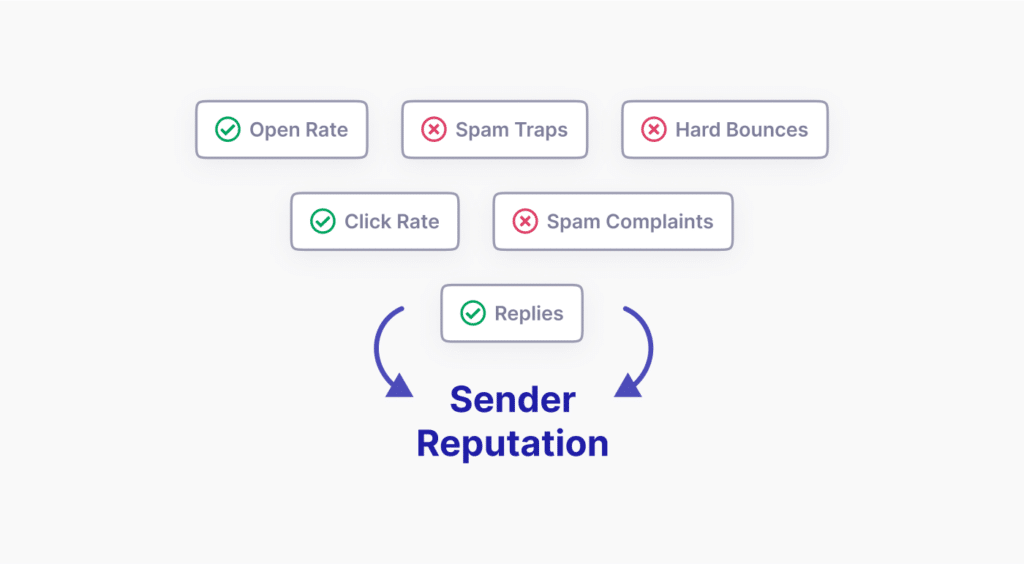
When email volume from a domain increases dramatically and unexpectedly, ISPs may apply additional scrutiny. This is because similar patterns are sometimes associated with compromised email accounts, bulk spam operations, or security issues with sending infrastructure. While this protective measure helps ISPs filter out genuine threats, it can also affect legitimate senders who experience unexpected volume spikes.
A card testing attack can potentially trigger rate limiting, impact inbox placement, and affect sender reputation metrics. The good news is that these issues are preventable with proper security measures.
Potential Impact on Email Performance
When sender reputation is affected by unusual sending patterns, several things can happen. Email delivery may be delayed as messages are queued for additional review. Some messages may be filtered to spam folders, and inbox placement rates can decrease. Transactional emails like order confirmations and password resets may experience delivery issues.
It typically takes 8 to 12 weeks to fully rebuild sender reputation after it has been negatively impacted, which is why prevention is so important.
The best approach is to implement security measures that prevent card testing attacks from happening in the first place, protecting both your payment security and your email infrastructure.
Volume Spikes vs. Spam Complaints: Understanding the Difference
Most site owners are familiar with how spam complaints affect email deliverability. Gmail and Yahoo require spam rates below 0.3%, and best practice is to aim for 0.1% or lower. Spam complaints typically accumulate gradually, giving you time to identify and address issues.
Volume spikes from card testing attacks present a different challenge because they happen suddenly and affect different metrics.
Multiple impact factors: Rather than just affecting complaint rates, volume spikes can influence sending pattern consistency, bounce rates (if fraudsters use invalid email addresses), engagement metrics (fraudulent submission emails typically have zero opens or clicks), and overall volume-to-engagement ratios.
Rapid onset: While spam complaints build over time, volume issues can emerge within hours during an active attack. ISPs use automated systems to flag unusual sending patterns, which means intervention happens quickly, often before you’re aware there’s a problem.
Timeline: How Card Testing Attacks Affect Email Delivery
Understanding the timeline of a card testing attack can help you recognize the signs early and take preventive action. Let’s take a look a typical timeline to get a better idea of exactly how fast an attack like this could affect your email deliverability:
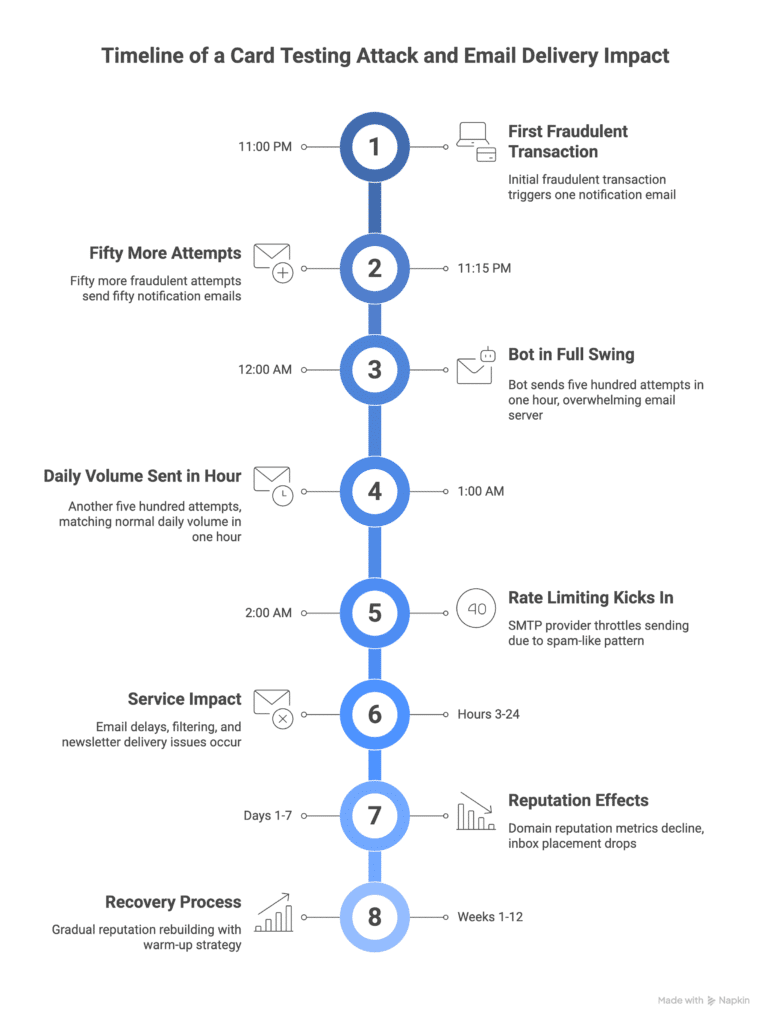
Stage 1: The Attack (Hours 0-3)
11:00 PM: The first fraudulent transaction comes through. One notification email sent.
11:15 PM: Fifty more attempts. Fifty notification emails.
12:00 AM: The bot is in full swing. Five hundred attempts in the last hour. Your email server is processing five hundred outbound emails.
1:00 AM: Another five hundred. Your normal daily volume is sent in a single hour.
2:00 AM: Rate limiting kicks in. Your SMTP provider starts throttling because your sending pattern is now indistinguishable from spam.
Stage 2: Service Impact (Hours 3-24)
If the attack continues unaddressed, email service may be affected. Password reset emails may be delayed, and order confirmations might experience delivery delays due to queue backup. Some notifications could be filtered or delayed as ISPs review unusual sending patterns, and newsletter delivery rates may temporarily decrease.
Stage 3: Reputation Effects (Days 1-7)
Even after stopping the attack, email performance may continue to be affected:
Your domain reputation metrics may show changes as ISPs process the unusual sending pattern. Email monitoring tools like Google Postmaster Tools might show reputation score decreases. Inbox placement rates could be lower than normal during this period.
This is why prevention is so much more effective than remediation.
Stage 4: Recovery Process (Weeks 1-12)
If sender reputation has been affected, rebuilding it requires a methodical approach. You must gradually rebuild your sending reputation through a process similar to “warming up” a new IP address. This involves a gradual increase in email volume over 15 to 60 days, starting with your most engaged subscribers.
How to Prevent Card Testing Fraud
One of the most effective ways to prevent card testing fraud is to set a minimum price on your payment fields. This simple configuration can stop thousands of fraudulent attempts before they happen.
Why Minimum Price Settings Work
The approach is elegantly simple but highly effective. When you set a minimum transaction amount on your payment fields (such as $5, $10, or $20), any transaction below that threshold won’t be processed.
Since fraudsters prefer micro-transactions between $0.50 and $2.00 (they’re less likely to trigger fraud alerts), setting a minimum price makes your form unattractive for card testing. Meanwhile, legitimate customers are unaffected because your actual products or services already cost more than the minimum.
Setting Up Minimum Prices
If you’re using WPForms, here’s how to configure minimum prices on your payment fields:
- Open your form in the form builder
- Navigate to the form with payment fields
- Select your Payment Single Item field
- Click on Field Options
- Find the “Minimum Price” setting
- Enter your minimum amount
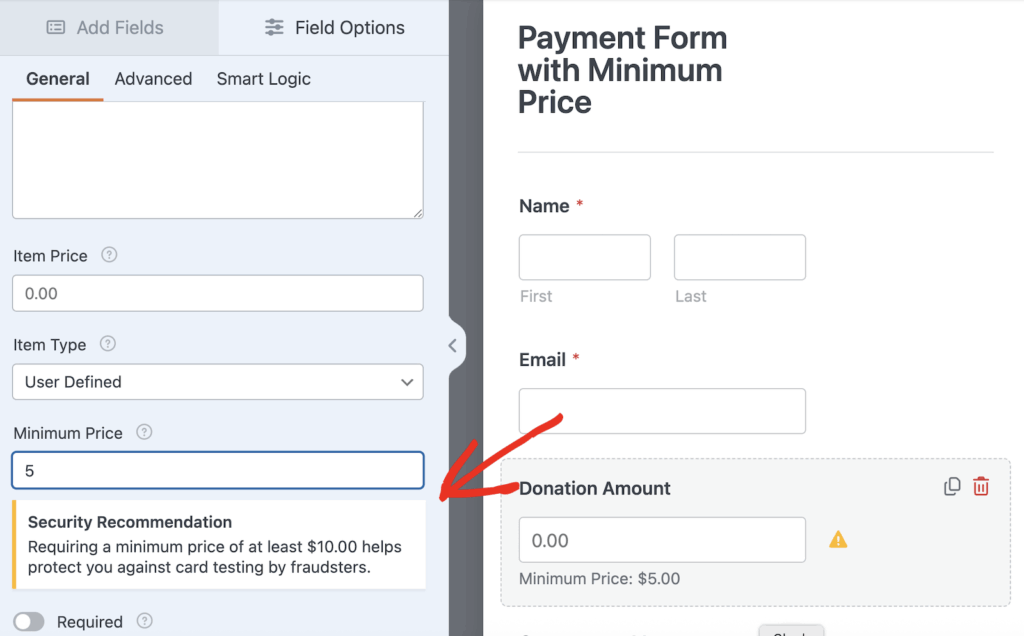
The key is setting it high enough to deter fraudsters but low enough not to impact your legitimate lowest-priced offering. For donation forms where visitors can enter custom amounts, even a $5 minimum provides significant protection without discouraging genuine donors.
The Complete Email Protection Strategy
Preventing card testing fraud requires multiple layers of protection. Here’s your complete defense strategy:
Layer 1: Prevent the Attack (Form Security Features)
Set minimum prices on all payment fields as your first line of defense. This setting alone can stop thousands of fraudulent attempts. This is especially important for donation forms where visitors can enter any amount.
Add CAPTCHA or an alternative to your forms to block automated bots from even reaching your payment fields. Most form plugins support Google reCAPTCHA v2 and v3.
For high-value forms, enable email verification to require users to verify their email address before submitting. You can also use conditional logic to show payment fields only after users complete required information fields, making automated attacks more difficult.
If you’re using Stripe for payments, enable Stripe Radar, their built-in fraud detection system that uses machine learning across millions of transactions to identify fraudulent patterns.
Layer 2: Proper Email Infrastructure (WP Mail SMTP)
Here’s the critical point most WordPress site owners miss: Never rely on WordPress’s default wp_mail() function for transactional emails.
Why? Because wp_mail() uses your web host’s mail server, which lacks proper authentication (SPF, DKIM, DMARC), uses shared IP addresses with poor reputation, has no throttling or queuing capabilities, can’t handle sudden volume spikes, and provides no logging or monitoring.
When a card testing attack hits, wp_mail() will attempt to send every single notification immediately, with no safeguards.
WP Mail SMTP routes your WordPress emails through a professional SMTP service provider, giving you several advantages:
Proper authentication through SPF, DKIM, and DMARC records that prove your emails are legitimate. ISPs heavily weight authentication when calculating sender reputation.
Dedicated infrastructure means your emails are sent through professional mail servers with established reputations, not your shared hosting server.
Rate limiting and queuing ensures that when volume spikes occur, emails are queued and sent at safe rates instead of triggering red flags.
Backup connections let you use a different email provider if your primary email service goes down temporarily.
Email logging tracks every email sent from WordPress. During an attack, you can see exactly what’s happening and how many emails were sent.
Better deliverability under pressure because professional SMTP providers are built to handle volume fluctuations and maintain deliverability during attacks.
Layer 3: Smart Notification Strategy
Audit all your form notifications and ask yourself these key questions:
Do you need to send an email for every submission? For payment forms, consider sending notifications only for successful payments, skipping notifications for declined transactions, or using conditional notifications to filter obvious fraud (such as not notifying if a transaction is under $1).
Can you consolidate notifications? Instead of one email per transaction, you might implement daily digest emails of all transactions, threshold notifications (only notify after 10 transactions), or SMS alerts for suspicious activity instead of emails.
Are you sending to the right people? Review your “Send To” settings to remove unnecessary recipients, use role-based addresses instead of personal emails, and consider sending to a ticketing system instead of email.
Layer 4: Monitoring and Alerts
Set up monitoring so you catch attacks early:
Google Postmaster Tools shows your domain reputation on a 4-level scale (bad, low, medium/fair, high) and alerts you to spam complaints, delivery errors, and authentication issues. This is particularly important for high-volume senders.
Microsoft SNDS provides feedback on your reputation with Outlook and Hotmail domains, while Sender Score offers a free numerical reputation rating from 0-100.
Enable WP Mail SMTP email logging to monitor outbound volume and set up alerts for unusual spikes. Use your form plugin’s entry management to watch for suspicious patterns like multiple submissions from the same IP, similar names, or micro-transactions.
Recognizing Card Testing Activity Early
Early detection of card testing activity helps you respond quickly and minimize any impact. Here are the patterns to watch for:
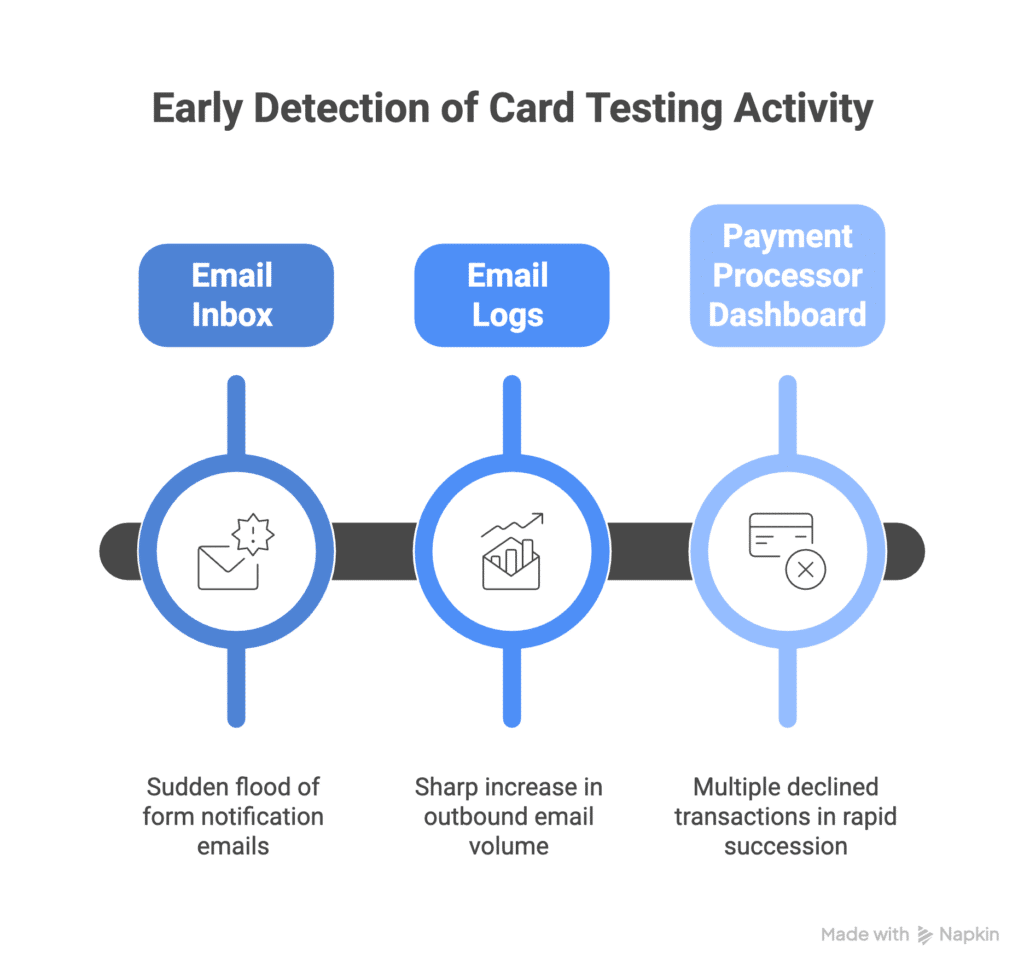
In Your Email Inbox: Watch for a sudden flood of form notification emails (dozens per hour instead of a few per day). The notifications typically show small amounts ($0.50-$5.00) with different names and email addresses but similar transaction patterns. You may see international email addresses or addresses that don’t match billing countries, with all submissions clustered within minutes or hours.
In Your Email Logs: Look for a sharp increase in outbound email volume (10x or more than your normal rate), with a high percentage of emails coming from payment form notifications. Failed delivery attempts may be increasing along with a climbing bounce rate.
In Your Payment Processor Dashboard: Multiple declined transactions in rapid succession are a red flag. Watch for different card numbers but the same shipping address, velocity alerts (many transactions per minute), a mix of international billing addresses, and cards being tested from countries flagged for fraud.
Email Deliverability Recovery Steps
If your email deliverability has been affected by a card testing incident, here’s a structured approach to recovery:
Immediate Actions (0-24 Hours)
Stop all attacks in progress by disabling payment forms temporarily or immediately enabling minimum price settings on your payment fields. Add reCAPTCHA if not already enabled, and block IP addresses showing fraudulent activity.
Assess the damage by reviewing WP Mail SMTP email logs to count how many emails were sent. Check sender reputation scores through Google Postmaster, Microsoft SNDS, and Sender Score. Test email deliverability to major providers (Gmail, Outlook, Yahoo) and check blacklist status using tools like MX Toolbox.
Implement damage control by contacting your SMTP provider immediately to explain the card testing attack. Ask about IP reputation status and any remediation options, and request guidance on recovery timeline.
Short-Term Recovery (Weeks 1-4)
Pause problem sends and implement a gradual re-warmup by starting with lower volumes and slowly increasing while prioritizing engaged users.
Week 1: Send only to subscribers who opened emails in the last 7-10 days. Reduce volume by 70-80% from normal, focus on your highest-value transactional emails, and monitor deliverability metrics daily.
Weeks 2-3: Expand to subscribers engaged in the last 30 days. Increase volume by 25% per week, continue monitoring bounce rates and spam complaints, and watch for improvements in sender reputation scores.
Week 4: Gradually add back less-engaged subscribers, approach 50-70% of normal volume, and look for stabilization in deliverability metrics.
Long-Term Prevention (Ongoing)
Implement all protection layers by keeping minimum price settings enabled permanently on all payment forms and maintaining reCAPTCHA on all payment forms. Use professional SMTP infrastructure for all WordPress emails and conduct regular security audits of form settings.
Establish monitoring routines including weekly checks of sender reputation scores, monthly email deliverability audits, quarterly security reviews of all forms, and automated alerts for volume spikes.
Stay current by keeping your form plugin updated (security patches often address fraud prevention), keeping your SMTP plugin updated, reviewing email authentication records annually, and staying informed about new fraud tactics.
Your payment forms and email infrastructure work together as part of your site’s overall communication system. When you secure one, you’re often protecting the other.
Setting minimum prices on payment fields provides an effective first line of defense against card testing fraud, helping prevent fraudulent attempts before they can generate excessive notification emails.
Using a professional SMTP solution like WP Mail SMTP ensures your legitimate emails are delivered reliably through proper infrastructure with authentication, rate limiting, and monitoring capabilities.
With the right configuration and tools in place, you can confidently accept payments while maintaining excellent email deliverability.
Next, Find Out More About How To Improve WordPress Email Security
Wondering about how secure WP Mail SMTP really is? Or do you just want to take further steps to improve your email security as a whole? Our guide to WordPress email security will help you out.
Ready to fix your emails? Get started today with the best WordPress SMTP plugin. If you don’t have the time to fix your emails, you can get full White Glove Setup assistance as an extra purchase, and there’s a 14-day money-back guarantee for all paid plans.
If this article helped you out, please follow us on Facebook and Twitter for more WordPress tips and tutorials.

